
Digital Fortress Guide to Web Shell Detection and Prevention
A web shell is a malicious script or program that cybercriminals deploy to gain unauthorized access and control over a web server or a website. It is essentially a backdoor or remote administration tool that allows attackers to interact with a compromised server, execute arbitrary commands, and manipulate files and data on the server. While web shells can serve legitimate purposes for system administrators who need remote access to manage their servers, they are often used nefariously by cybercriminals for illegal activities.
Web applications and websites are integral to our daily lives. However, this digital landscape also poses numerous security challenges. Among the most insidious threats is the use of web shells, malicious scripts or programs that attackers deploy to exploit vulnerabilities and gain unauthorized access to web servers. To protect your digital fortress, it's crucial to understand web shell detection and prevention techniques. In this article, we'll provide a comprehensive guide to help you safeguard your online assets.
Understanding Web Shells

Web shells are typically small scripts or code fragments that are injected into web servers. Once inside, they can execute arbitrary commands, steal data, distribute malware, and even provide a backdoor for persistent access. Attackers can deploy web shells through various means, including exploiting vulnerabilities in web applications, phishing attacks, or via stolen credentials.
Here are some key characteristics of web shells:
⭕ Remote Access: Web shells provide remote access to a compromised server or website, allowing attackers to control it from a distance. This access can include executing commands, uploading or downloading files, and modifying system configurations.
⭕ Stealthy: Web shells are designed to be discreet and hard to detect. They are often hidden within legitimate website files or directories, making it challenging for security professionals to identify their presence.
⭕ Command Execution: Attackers can use web shells to execute commands on the server, enabling them to perform various actions, such as viewing system information, deleting files, or even launching more advanced attacks.
⭕ Data Exfiltration: Web shells can be used to steal sensitive data from the compromised server, such as user credentials, databases, or other valuable information.
⭕ Persistence: Once a web shell is deployed on a server, attackers may aim to maintain persistent access, ensuring they can continue to control the system even if their initial point of entry is discovered and closed.
⭕ Remote Code Execution: Some web shells allow attackers to upload and execute arbitrary code, which can lead to full system compromise.
⭕ Authentication Bypass: In some cases, web shells are used to bypass authentication mechanisms on web applications, granting unauthorized access to restricted areas.
It's important to note that the use of web shells is illegal and unethical unless authorized for legitimate system administration purposes. To protect against web shell attacks, organizations and website owners should implement strong security practices, regularly update software and plugins, and conduct security audits to detect and remove any potential threats.
Types of Web Shells
Web shells come in various forms and can be written in different programming languages. Here are some common types:
⭕ PHP Web Shells: These are scripts written in PHP and are commonly used to exploit vulnerabilities in PHP-based web applications. They are often disguised as benign PHP files.
⭕ ASP/ASP.NET Web Shells: These are written in languages like ASP or ASP.NET and target servers running Microsoft technologies. JSP Web Shells: Written in Java Server Pages (JSP), these target Java-based web applications.
⭕ Python/Ruby Web Shells: Some attackers prefer using scripting languages like Python or Ruby to create web shells, as they are versatile and can be used on various platforms.
⭕ Client-Side Web Shells: These are scripts that run on a user's browser, typically JavaScript-based, and are used to exploit client-side vulnerabilities.
How Attackers Deploy Web Shells
Attackers use various techniques to deploy web shells on target servers or websites, including:
⭕ Exploiting Vulnerabilities: They may identify and exploit vulnerabilities in web applications, content management systems (CMS), or plugins to upload a web shell.
⭕ File Upload Forms: If a web application allows file uploads, attackers may upload a malicious file (the web shell) disguised as a benign file type, such as an image or document.
⭕ Remote File Inclusion (RFI): RFI attacks involve including external scripts or files hosted on the attacker's server, which can lead to the execution of a web shell.
Web Shell Use Cases
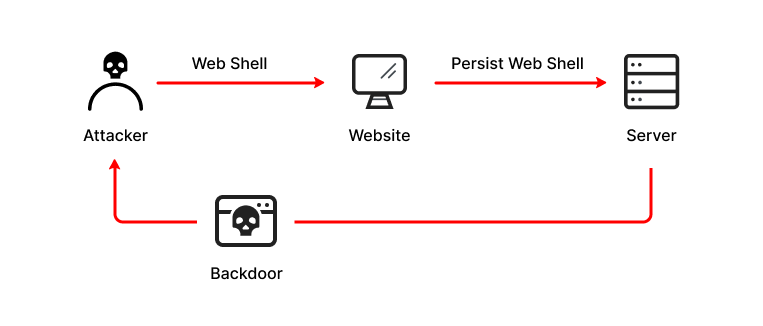
Web shells can be leveraged for a range of malicious activities:
⭕ Data Theft: Attackers can use web shells to steal sensitive data, including user credentials, customer information, and databases. Defacement: Web shells enable attackers to deface websites, leaving behind a visual message or changing the website's content.
⭕ Distributed Denial of Service (DDoS): Web shells can be used to launch DDoS attacks by instructing the compromised server to flood targeted websites or services with traffic.
⭕ Propagation: Cybercriminals can use web shells to move laterally within a network, spreading their influence and compromising additional servers or devices.
The Importance of Detection
Detecting web shells promptly is critical to preventing significant damage. Here are some common signs that your web server may be compromised:
⭕ Unusual File Modifications: Monitor your server's file system for unexpected changes, especially in web directories. Look for new, unfamiliar files or altered timestamps on existing files.
⭕ Abnormal Network Activity: Use network monitoring tools to spot unusual traffic patterns or connections originating from your server. This could indicate unauthorized access.
⭕ High Resource Usage: Web shells often consume server resources, leading to increased CPU or memory usage. Regularly check server performance metrics for anomalies.
⭕ Suspicious User Accounts: Review user accounts with elevated privileges. Unauthorized accounts or changes to existing accounts may indicate a breach.
Web Shell Detection Techniques
Effective detection relies on a combination of tools, techniques, and best practices. Here are some key methods:
⭕ Antivirus and Security Software: Employ up-to-date antivirus and security software to scan your server for known web shell signatures.
⭕ File Integrity Monitoring (FIM): FIM tools monitor file changes and can alert you to unauthorized modifications.
⭕ Web Application Firewalls (WAFs): Implement a WAF to filter incoming traffic and block known web shell payloads.
⭕ Behavioral Analysis: Use behavioral analysis tools to detect unusual patterns of activity on your server.
⭕ Regular Auditing: Conduct periodic security audits to identify vulnerabilities that could be exploited by attackers.
⭕ Access Control: Implement strong access controls and restrict file upload capabilities on your web server.
Prevention Strategies
While detection is crucial, prevention is equally important. Here are some preventive measures to consider:
⭕ Patch and Update: Keep your web server software, applications, and plugins up to date to minimize vulnerabilities. Least Privilege Principle: Limit user privileges to only what is necessary to perform their tasks. This reduces the potential impact of a breach.
⭕ Strong Authentication: Enforce strong password policies and implement multi-factor authentication to prevent unauthorized access.
⭕ Access Control Lists (ACLs): Use ACLs to restrict access to critical server directories and files.
⭕ Security Education: Train your staff to recognize phishing attempts and social engineering tactics that could lead to web shell deployments.
⭕ Firewalls and Intrusion Detection Systems: Use firewalls and IDS/IPS systems to monitor and block suspicious network traffic.
FAQ for Digital Fortress Guide to Web Shell Detection and Prevention

What is a Web Shell?
A web shell is a malicious script used by attackers to gain persistent access and remote control over a compromised web server. It acts as a backdoor, allowing the execution of arbitrary commands and the theft of sensitive data.
How do Web Shells get installed?
Web shells are typically installed by exploiting vulnerabilities in web applications, such as SQL injection, remote file inclusion (RFI), and insecure file upload functionalities. Attackers may also leverage weak server configurations or stolen credentials.
Why is it important to detect and prevent Web Shells?
Undetected web shells can lead to significant security breaches, data theft, website defacement, and server hijacking. They allow attackers to maintain access to the server, even after the initial vulnerabilities are patched, making them a critical threat to web security.
What are the signs of a Web Shell?
- Unexpected Files or Scripts: Presence of unfamiliar files or scripts in the server directories.
- Unusual Web Traffic: Spike in traffic, especially from unusual locations or IP addresses.
- Modified Files: Unexpected changes to files or directories on the server.
- Slow Server Performance: Unexplained slowdown in server performance can indicate unauthorized activities.
- Error Logs: Suspicious entries in server logs, such as unusual command executions.
How can I detect Web Shells?
- Regular Audits: Conduct regular file and directory audits to check for unauthorized changes or additions.
- Log Analysis: Monitor and analyze web server logs for unusual activities.
- File Integrity Monitoring: Use tools to monitor file changes in real-time.
- Web Application Firewalls (WAF): Deploy WAFs to detect and block malicious traffic.
- Antivirus and Anti-malware: Use security software designed to detect web shells and malware.
How can I prevent Web Shell installation?
- Patch and Update: Regularly update all software, including the web server, CMS, and plugins.
- Secure File Uploads: Implement strict validations on file uploads, limiting file types and employing antivirus scanning.
- Least Privilege Principle: Limit permissions and access rights to the minimum necessary for functionality.
- Use Strong Passwords: Implement strong password policies and consider using multi-factor authentication.
- Network Segmentation: Isolate critical systems and databases from public-facing servers.
Can Web Shells be removed manually?
While it's possible to remove a web shell manually by deleting the malicious file, this approach doesn't address the underlying vulnerabilities that allowed its installation. Additionally, attackers might have installed multiple backdoors or created hidden persistence mechanisms. Therefore, it's recommended to restore from a known good backup after identifying and patching the vulnerabilities.
Are there tools to help detect and remove Web Shells?
Yes, there are several tools and scripts available to help detect web shells, including antivirus and anti-malware solutions with web shell signatures, specialized web shell scanners, and intrusion detection systems (IDS). However, removal should be handled carefully, preferably by experienced cybersecurity professionals, to ensure that all components of the attack are eradicated.
What should I do if I find a Web Shell on my server?
- Isolate: Disconnect the compromised server from the network to prevent further damage.
- Analyze: Investigate how the web shell was installed and identify all affected files.
- Clean: Remove the web shell and any other malware found. Repair or restore affected files from backups.
- Patch: Address the vulnerabilities that allowed the web shell installation.
- Monitor: Increase monitoring and logging to detect any further attempts or remaining vulnerabilities.
How often should I check my website for Web Shells?
Regular checks are crucial for maintaining the security of your website. The frequency depends on various factors, including the size of your website, the volume of traffic, the sensitivity of the stored data, and the current threat landscape. For most organizations, a weekly review of logs and a monthly comprehensive security audit, including a search for web shells, are advisable. High-traffic or high-risk websites might require more frequent checks.
Can Web Shells affect all types of web servers and hosting platforms?
Yes, web shells can affect any web server or hosting platform where the attacker can exploit vulnerabilities to upload malicious scripts. This includes popular web servers like Apache, Nginx, and IIS, across all operating systems. No platform is inherently immune; the key is effective vulnerability management and security practices.
Is it enough to just delete a detected Web Shell?
Simply deleting a detected web shell is not enough. While removal is a necessary step, it's crucial to conduct a thorough investigation to understand how the web shell was uploaded in the first place. This involves identifying and patching the exploited vulnerability, checking for additional backdoors or malware, and improving security measures to prevent future incidents.
What are the legal implications of a Web Shell breach?
The legal implications can vary depending on the jurisdiction, the nature of the data compromised, and the impact of the breach. Generally, organizations may face regulatory fines, lawsuits, and reputational damage, especially if the breach involves customer data and the organization failed to implement adequate security measures. Compliance with data protection laws, such as GDPR in Europe, also requires prompt breach notification procedures.
How can I educate my team about Web Shells and their risks?
Education is a vital component of cybersecurity. Consider the following steps to educate your team:
- Training Sessions: Conduct regular training sessions on cybersecurity best practices and the latest threats, including web shells.
- Security Policies: Develop clear security policies and procedures, ensuring that all team members are aware of their roles in maintaining security.
- Simulation Exercises: Run simulated cyber attack exercises, including scenarios involving web shell breaches, to test and improve your team's response capabilities.
- Resources: Provide access to educational resources, such as articles, online courses, and workshops, focusing on web security.
- Culture of Security: Foster a culture of security within the organization, encouraging vigilance and prompt reporting of any suspicious activities.
Conclusion
Web shell attacks are a persistent threat in the ever-evolving landscape of cybersecurity. To defend your digital fortress effectively, it's essential to understand the nature of these threats and implement a robust strategy for detection and prevention. By staying vigilant, keeping your systems updated, and following best practices, you can significantly reduce the risk of falling victim to web shell attacks and protect your online assets. Remember, in the world of web security, proactive defense is the key to success.





